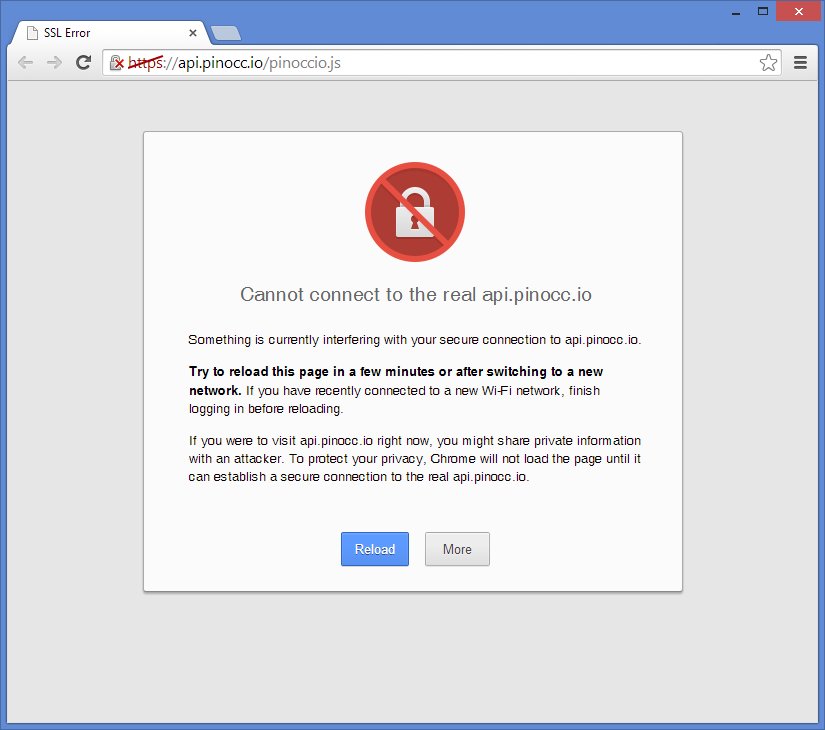
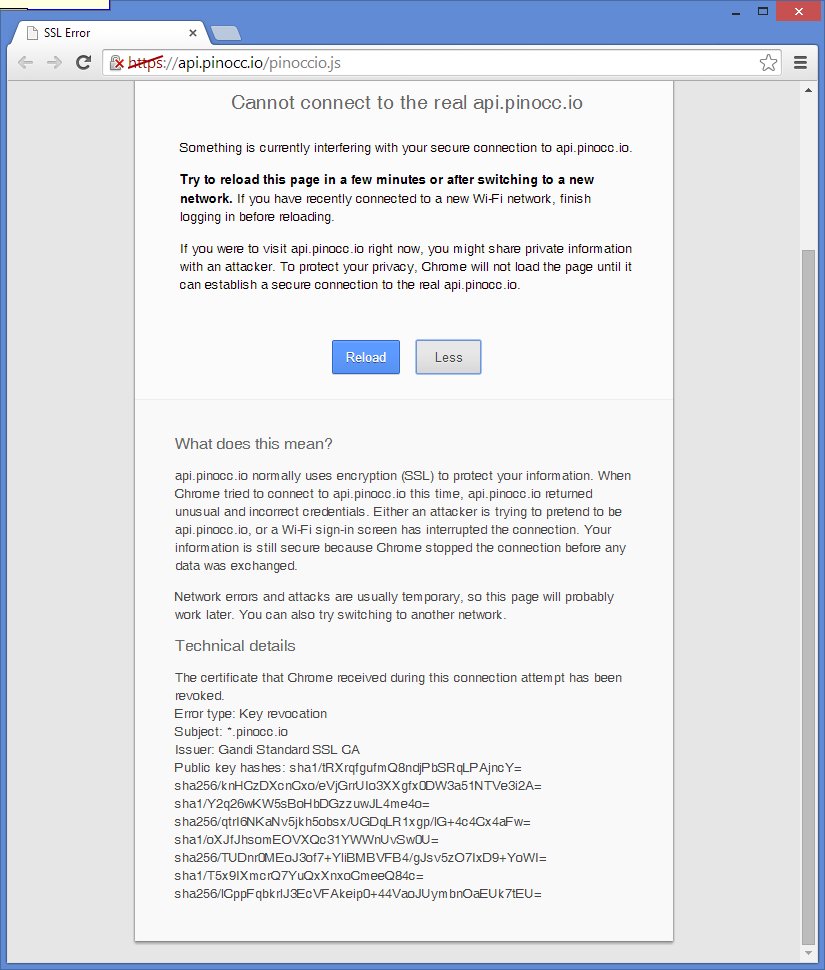
We are pleased to announce that IRLib has been updated to version 1.5. IRLib is a library for Arduino-based microcontrollers that allows for the receiving, decoding, and sending of infrared signals. These new changes are a step forward in making the library less hardware platform dependent so that it can be more easily used by a variety of microcontrollers. These changes include…
- New bit-bang option for PWM output frequency setting. Now can use any output pin with no hardware timers. Note:bit-bang output not as accurate as timer-based frequency selection.
- Major rewrite of IRLibTimer.h to facilitate bit-bang. Separated hardware timer selection and specification into sending and receiving sections in order to implement bit-bang.
- New IRfrequency class for detecting input frequencies. Previously was a stand-alone special sketch but now is a class including a DumpResults method.
- New IRfreq and IRrecvDumpFreq illustrate simultaneous detection of frequency and pattern with both an IR learner and IR receiver is connected.
- New #define USE_IRRECV define can be commented out to completely remove the interrupt driven IRrecv receiver class from the library. This resolves ISR conflicts with other libraries such as Tone() when not using IRrecv class.
- New #define USE_DUMP define can be commented out to disable DumpResults methods. Saves code space when these methods are not needed.
- Revised user manuals to document new features and correct previous documentation problems.
Note: The included user manual update is not yet available on the website at http://tech.cyborg5.com/irlib/docs/ but it will be updated shortly. New user manual is available with the library itself as a Microsoft Word .docx file as well as PDF and EPUB versions.
This library is available on GitHub at . For more information on this library see http://tech.cyborg5.com/irlib/